I’m a bit confused. I got an email from someone who isn’t part of our IT department saying I need to update my email account. Is it legit or some sort of scam?
Whatever company you work for, however big your IT department is – or isn’t! – one of the most important characteristics of people who can stay safe in the modern online world is skepticism. It sounds awful, but stop trusting people. Stop trusting the email you receive, stop assuming there a Nigerian prince who just happened to pick you to send a few million dollars. Stop believing that some unknown person in “IT” wants to help you reset your password, regain access to your account or upgrade you to the next version of the software.
They’re all scams, they’re all bad guys trying to part you from your account credentials, your password, your personal information or even your money directly. If it sounds too good to be true, well, it is. The problem is that on the Internet the cost of sending a message to hundreds of thousands or even millions of people is essentially the same as sending it to a few dozen. So the scammers do just that, scattering their scams and hustles to the four winds in the hope that 0.01% of people will respond favorably. Send it to a million people and 0.01% is still 100 suckers.
I don’t know exactly what message you received, but I get these sort of “IT department” emails all the time. Let me show you how they work and then I’ll also explain the sender’s goal too.
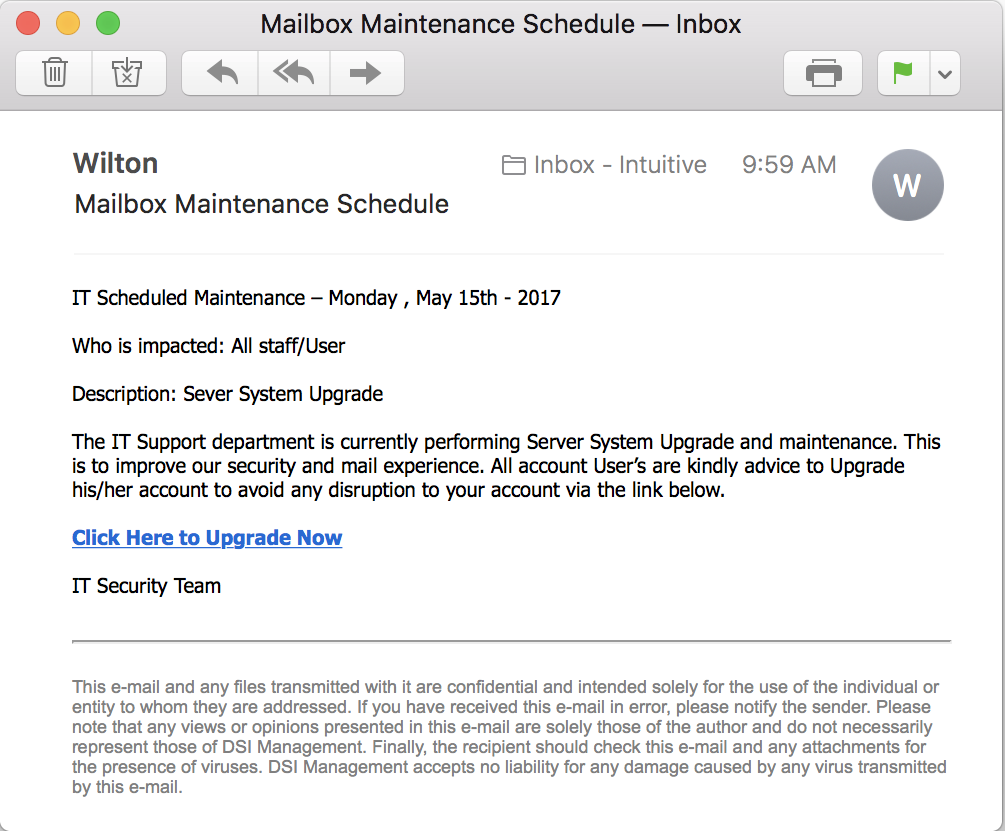
Seems legit, right? Except I don’t have an IT Support department so even on the face of it, this makes no sense. You might be part of a big enough organization that you do have a support team, but this still looks pretty questionable, not the least of which is the typo “Sever” in the Server System Upgrade.
But even if it all looks 100% legit, once you move your cursor over the “Click Here to Upgrade Now” link, your email program should show you the target or destination URL:
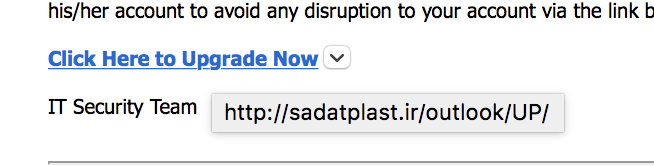
The “.IR” domain is Iran. Does your IT department work with servers in Iran? I didn’t think so.
Still, what if you did click on this link? Then you’ll go to an Outlook.com login screen that certainly looks legit:
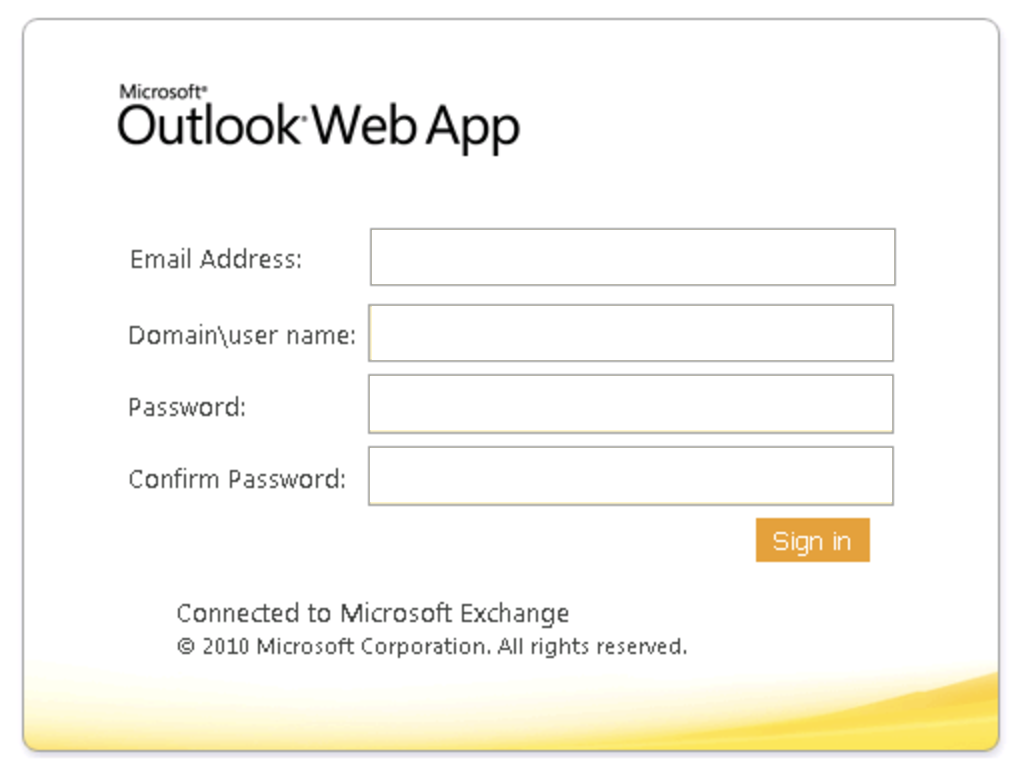
At this point all the alarm bells in your head should be going off. Why are you supposed to log in to a server in Iran to update your Outlook Web App access? Their goal should be obvious by this point, however: you enter your login and password information, then they promptly log in to your real account at Microsoft.com and change the account password. That’s it, you’re now locked out of your own account and they can explore your mailboxes and sent email at their leisure.
This is called a phishing attack and the goal is to trick that password out of you. And it’s dangerous because smart hackers can glean quite a bit out of just your email messages, and then use it to get new credit cards, buy products shipped to them, not you, use your email account to spread a virus, and much worse.
To avoid these sort of things, teach yourself to always check links before you click them, verify legitimacy of emails from others, and triple check displayed URLs before you enter any data on a page you reached from an email link.
Oh, and if you did “sign in” on the above screen, here’s where you’re taken:
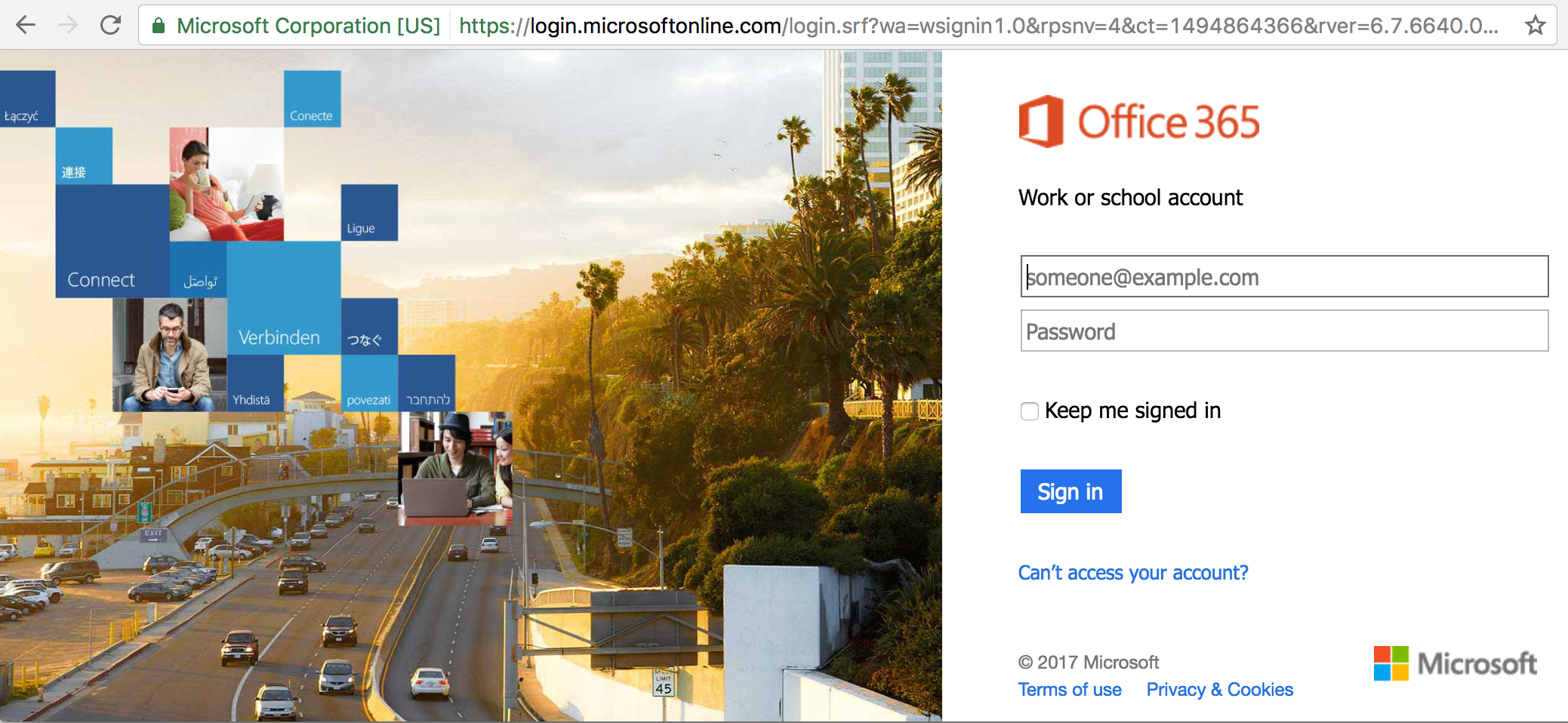
Smart, really. The real Microsoft Online site. You log in to the bogus site, and it bounces you here and prompts you to sign in again. Like most people you’ll probably just shrug and dutifully re-enter your login information, forgetting that you just gave your account credentials to some bad guy half-way around the world.
So please, be careful out there!
