I’m extremely skeptical of emails that I receive, particularly those that seem to be from a major company like Google or a bank. There are too many scams out there. But when I got an email from Apple about my AppleID, it looked mostly legit. Until I looked closer…
Most phishing attacks, as they’re known, are trivial to identify. They’re from a weird and inexplicable email address, they are rife with spelling errors or they’re from an organization or institution that you don’t actually have an account with. Easy to spot. But every so often one slips through your skeptical filter and it then becomes a matter of being a detective to see if the message you’ve received is legit or bogus.
Even things like “is the Web site secure and running SSL” isn’t enough to differentiate legitimate queries and email messages from junk. But I’m getting ahead of myself now. Let’s have a look at the email I got that notified me that “Your Apple ID account has been locked due to login from an unauthorized device.” A close read will identify the grammatical error (“due to a login” would make more sense) but you can’t be too narrowly focused because even legit notifications could theoretically have grammatical errors in them, right? Even Apple.
Here’s the email I received:
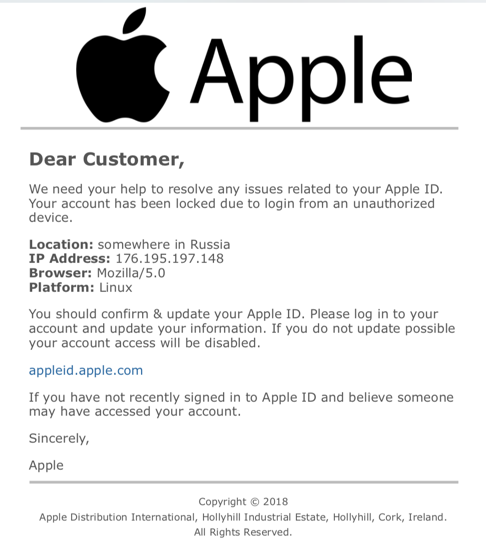
The logo is a bit odd for Apple email and it’s hard to understand why an Apple facility at Hollyhill Industrial Estate in Cork Ireland would be sending this message, but it seems reasonably believable nonetheless, and a Linux hacker in Russia? Definitely sounds sketch!
Slow down and look at where the link is going to take you, however. A simple “hover” over the appleid.apple.com shows the problem:
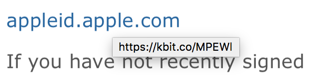
Apple would hardly use a shortened URL to hide the destination for the click, so at this point I’m highly skeptical and am sure it’s bogus. But let’s follow the trail and see where it leads…
A click on the kbit.co shortened URL and it redirects as expected, dropping me here:

As you can see, Chrome is showing this as a secure link, though where’s “apple” in the domain name? A close look shows that the domain in question is support-custhelp.com, which is also a bit suspicious. And yet, it’s secure. Click on the Secure padlock and you’ll find there’s even a security certificate:
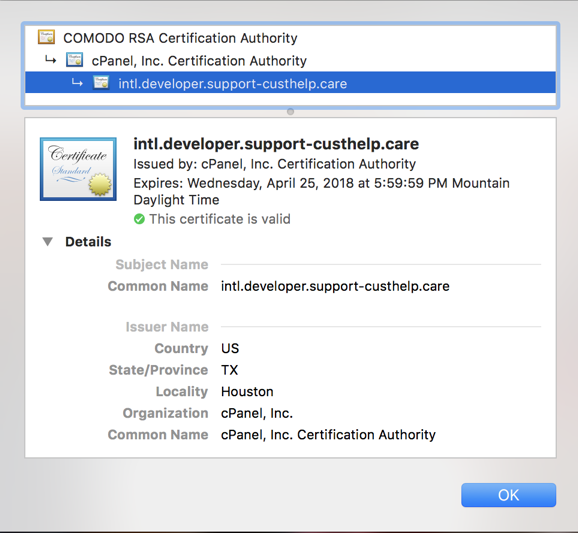
Still, it’s bogus. One easy way to tell: Enter garbage information and see what happens. I do just that with an email address of “bite@me.com” and a password of “nonononono”. It works! Amazing. 🙂
Here’s what I see next:

Smart, eh? Now they want me to pick whichever of my standard security questions I use and enter its answer. Noooot so much.
I make a random choice, enter a random answer, click “next” and the next screen is bound to cause anxiety in even the most calm and relaxed of users:

Of course nothing’s been locked, nothing’s happened, it’s all bogus. Most people at this point might be anxious so they click on “Unlock Account” and this is where you can see the nefarious identity theft aspect of this phishing attack:

There’s no reason that Apple would ever ask for your social security number – and I would advise against using it for any site online – but if you were to fall for this scam, filling in this last page would really be a disaster for your personal information. But it looks so real, right?
That’s why it’s critical that you remember the modern Internet mantra: don’t trust any site, don’t trust any email.
Now, be careful out there.
