Both the FBI and the Federal Communications Commission have recently warned people about the dangers of “juice jacking”. It’s having malware installed on your phone by using a public access charging station. Here’s how to avoid it happening to you and an examination of whether it’s actually a real threat or not…
The threat seems scary enough; plug in your precious smartphone into a public charging device and when you pick it up 30 minutes later, all charged up, it also now has malicious apps installed and your private information has all been surreptitiously pulled off the device. The technical term for this is juice jacking and the FBI and FCC have both issued public warnings about the threat.
But is it legit?
When you plug your phone – Android or iPhone – into what’s known as a trusted device, there is a certain amount of information that can flow back and forth on that charging wire. It’s how people do backups, copy photos, and even remote-access apps in some situations. Very helpful. The question then is whether it’s possible to spoof a trusted relationship with an otherwise unknown device and the answer is that it’s not. In fact, smartphone developers are very careful about this sort of access because you can imagine how upset people would be if it were a threat vector.
Even the FCC in its latest warning observes “Although “juice jacking” has been demonstrated to be technically possible as a proof of concept, the FCC is not aware of any confirmed instances of it occurring.” In other words, it’s theoretically possible but it’s never once actually been done in any charging station anywhere in the world.

Public charging stations certainly seem benign, but that’s because they really are innocuous. The biggest threat you are likely to face is “dirty” power going into your device, but modern devices can handle a wide variety of voltages and, worst case, are more likely to just not charge than to incur any damage to your device.
The concern is if there’s a computer hidden within the charging system that is spoofing a trusted device relationship, but as I’ve already said, that really can’t happen. Nonetheless, it’s smart to understand how your phone also helps you avoid this risk too, so let’s have a look.
TRUSTED DEVICES CONNECTED TO AN IPHONE
Plug your iPhone or iPad into a charging device and it’ll start charging. The white battery icon will turn green and it’ll indicate the current charge state. Easy:
![]()
Plug it into a computer, however, and you’ll see this pop up:
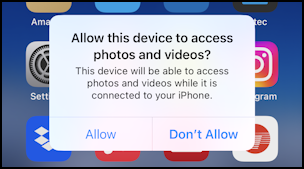
This is the trusted device prompt and your default response should always be “Don’t Allow“. More importantly, however, if you’ve plugged your phone into what you think is a simple charger and you’re seeing this prompt, then there is something fishy going on and you need to unplug it and find a different source of power. I’ve never seen this happen, but I suppose it’s theoretically possible.
However, note that in the “juice jacking” situation outlined by the FBI & FCC, that’s what you’d actually see with an iPhone, it wouldn’t just silently let the external device access data and add new apps or spyware to the phone. If there’s a sign encouraging customers to “Allow”, then I wouldn’t be plugging my devices in even if they were at 0%.
DETERMINING USB CHARGING ACCESS IN ANDROID
Smartphones running Android are a bit more tricky because you might indeed have your phone set to trust connections so when you think you’re just charging, you’re actually allowing access to your file system. For example, with my Pixel 6 Pro, when I plug it into a previously unknown Windows laptop, it simply indicates that it’s started charging, with no prompt indicating that the connection is more than just power.
Open up the phone and swipe down, however, and notifications reveals the nature of the connection:
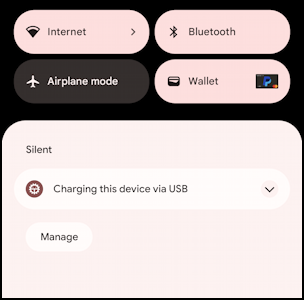
The prompt “Charging this device via USB” means it’s all good. Tap on the notification anyway, and you’ll go into an area in Settings that’s all about what permissions you grant that USB port on the device when it’s plugged in:
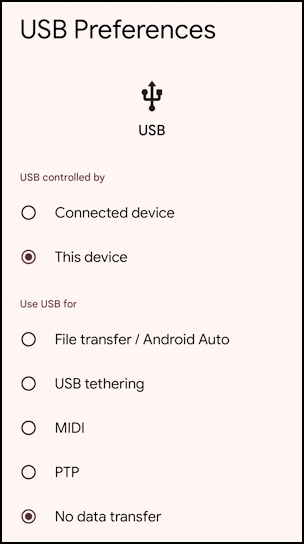
Many of these are related to debugging and software development, but generally you want to ensure that you have selected “This device” for the “USB Controlled by” section, and “No data transfer” for the “Use USB for” section, as shown above. Allowing the remote device to control the device is obviously dangerous, though allowing file transfer, USB tethering, MIDI (a musical device interface), and PTP (picture transfer protocol) vary in their risks depending on how you use your phone. Certainly when you’re plugged into an unknown device “No data transfer” is your friend.
THE LONG AND SHORT OF IT
The reality is that while there aren’t any reported instances of actual juice jacking, it is theoretically possible to create what appears to be a benign device charger that can be more malicious depending on your device settings and your ability to be fooled. If it says “Get free games: Just allow “File transfer” in Settings!!” or “Make us a Trusted Device, we’ll download beautiful new landscape photos as your device charges” then run the heck away from that device. At that point it’s dangerous, but one hopes that incredibly few people would be taken in by something of this nature.
I mean, you wouldn’t believe it, would you?
Pro Tip: I have quite a few tutorials and articles on computer basics and security. Please check out my computer basics help library and my spam, scams, and security article repository while you’re visiting. Thanks!

My laptops all have their own power/charging adapters as do my phone and tablets, so it is unlikely that I’ll ever need to use a charging station (I prefer using my own chargers). With that said, if such a need should ever arise, I’ll first ensure that any tethering is disabled, something I would have done prior to reading this item. I’d also suggest that anyone who connects their phone to a public charging station first ensure that the device is not in developer mode as well (enabling developer mode disables some of the phone’s security features).
Ernie